Security Scan
It’s easy to feel overwhelmed when you’re juggling multiple tasks and goals. Using a chart can bring a sense of structure and make your daily or weekly routine more manageable, helping you focus on what matters most.
Stay Organized with Security Scan
A Free Chart Template is a useful tool for planning your schedule, tracking progress, or setting reminders. You can print it out and hang it somewhere visible, keeping you motivated and on top of your commitments every day.

Security Scan
These templates come in a variety of designs, from colorful and playful to sleek and minimalist. No matter your personal style, you’ll find a template that matches your vibe and helps you stay productive and organized.
Grab your Free Chart Template today and start creating a more streamlined, more balanced routine. A little bit of structure can make a big difference in helping you achieve your goals with less stress.

National Retail s Timely Collaboration With Ignite Systems Amidst Cyber
Jun 13 2025 nbsp 0183 32 IBM s definition of cybersecurity Learn how modern threats evolve with technology stay ahead with trends and access the latest security reports Jan 27, 2025 · What is tokenization? In data security, tokenization is the process of converting sensitive data into a nonsensitive digital replacement, called a token, that maps back to the …

What Is Cybersecurity Forage
Security ScanAug 12, 2024 · Mobile Security Mobile Security umfasst Cybersicherheitstools und -praktiken, die speziell für Smartphones und andere Mobilgeräte gelten, einschließlich Mobile Application … IT Sicherheit sch 252 tzt die Computersysteme eines Unternehmens vernetzt digitale Daten vor unbefugtem Zugriff Datenschutzverletzungen Cyberangriffen und anderen b 246 swilligen
Gallery for Security Scan

Security For All Sectors The Formative Group Trowbridge

Top ICT Tenders Consumer Commission Looks To Security ITWeb

What Type Of Security Is Best For You Taybar Security

Security And The Right To Security Gentil Kasongo

How To Maintain Business Security When You re Not There AtulHost

The Top 3 Security Threats Developers Need To Defend Against Right Now
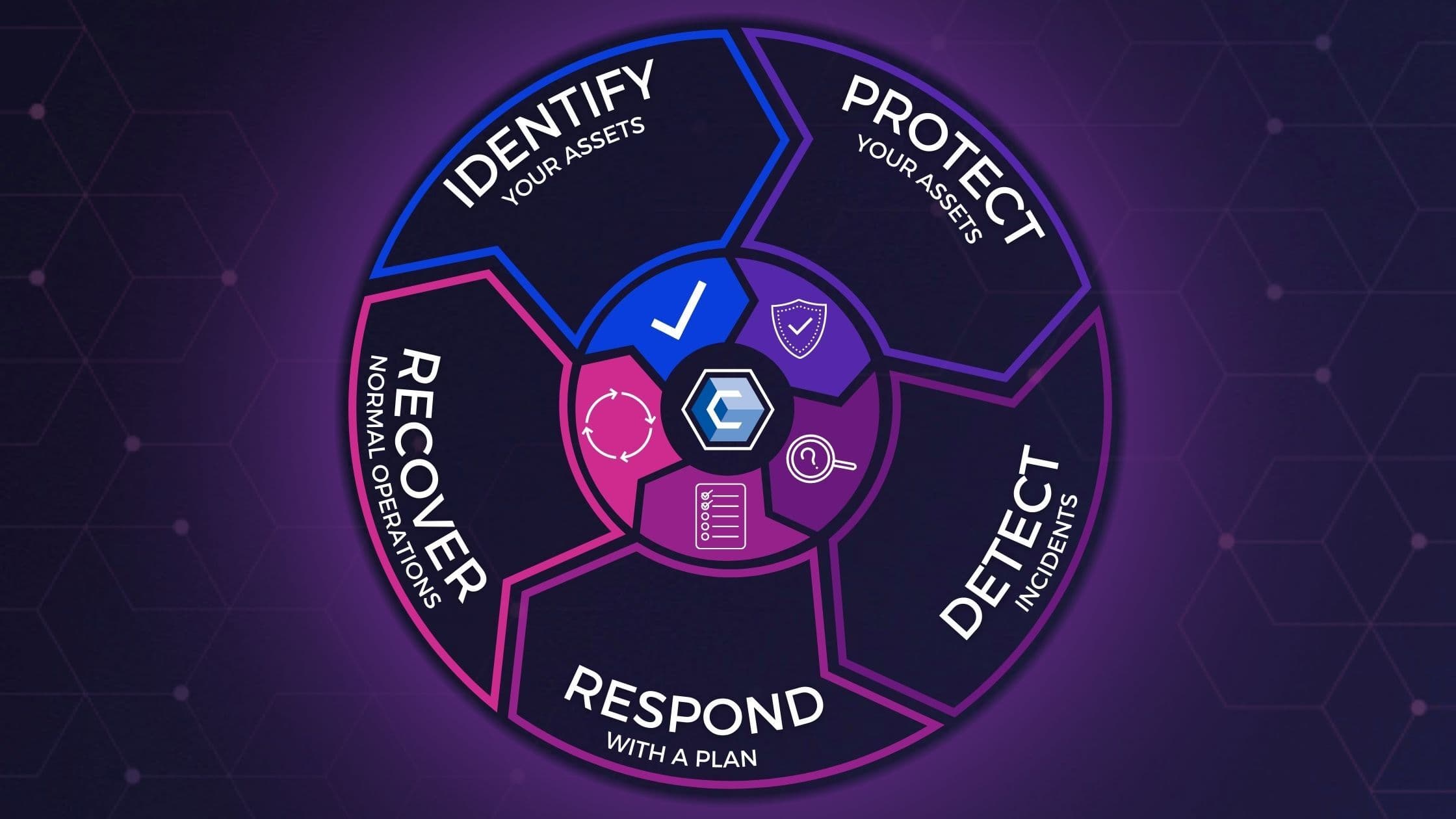
Reviewing The 5 Stages Of The Cybersecurity Lifecycle EXAMPLES

Cyber Security Saiba O Que Faz Um Profissional De Ciberseguran a

Understanding The 3 Phases Of Cybersecurity Architecture Ardoq
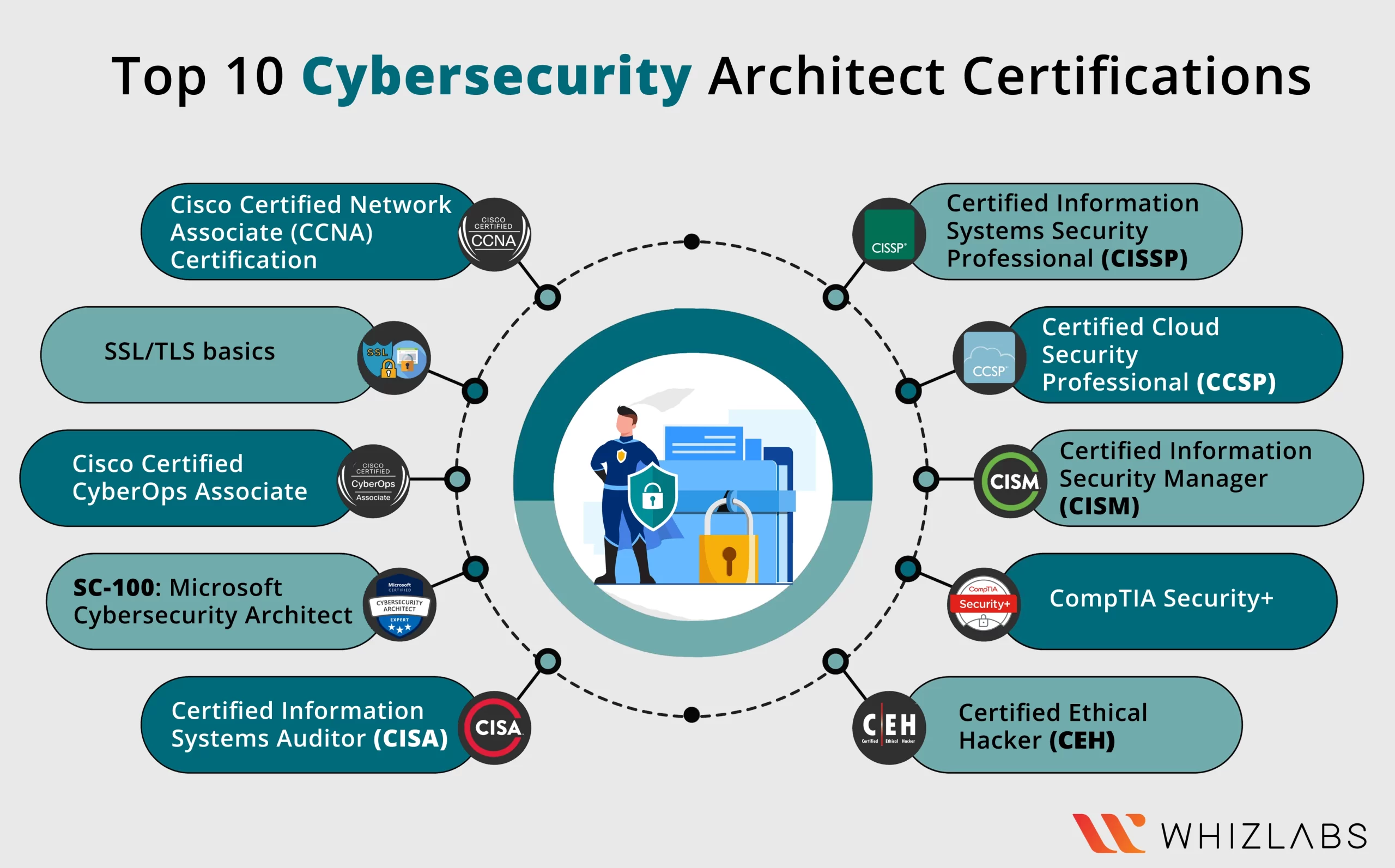
10 Best CyberSecurity Architect Certifications In 2024