Security Log Sheets Printable
It’s easy to feel scattered when you’re juggling multiple tasks and goals. Using a chart can bring a sense of structure and make your daily or weekly routine more manageable, helping you focus on what matters most.
Stay Organized with Security Log Sheets Printable
A Free Chart Template is a useful tool for planning your schedule, tracking progress, or setting reminders. You can print it out and hang it somewhere visible, keeping you motivated and on top of your commitments every day.

Security Log Sheets Printable
These templates come in a range of designs, from colorful and playful to sleek and minimalist. No matter your personal style, you’ll find a template that matches your vibe and helps you stay productive and organized.
Grab your Free Chart Template today and start creating a smoother, more balanced routine. A little bit of structure can make a big difference in helping you achieve your goals with less stress.

5 Security Measures That Experts Follow and So Should You Panda
IBM s global Cost of a Data Breach Report 2025 provides up to date insights into cybersecurity threats and their financial impacts on organizations La seguridad informática protege los sistemas informáticos, las redes y los datos digitales de una organización contra el acceso no autorizado, las filtraciones de datos, los ataques cibernéticos …

Bolstering Cybersecurity Readiness In The Cloud Information Age
Security Log Sheets PrintableJul 9, 2025 · Don't want to fork over $30 for a one-year subscription to Windows 10 Extended Security Updates? Microsoft is offering a couple of ways to avoid the fee. But there is a catch. Jan 27 2025 nbsp 0183 32 What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the
Gallery for Security Log Sheets Printable
.jpg#keepProtocol)
Cybersecurity Issues In Healthcare Today

What Is Cybersecurity Forage

Security And The Right To Security Gentil Kasongo

Cybersecurity Plan 3 Keys For CISOs Trend Micro US

Cybersecurity Issues And Challenges
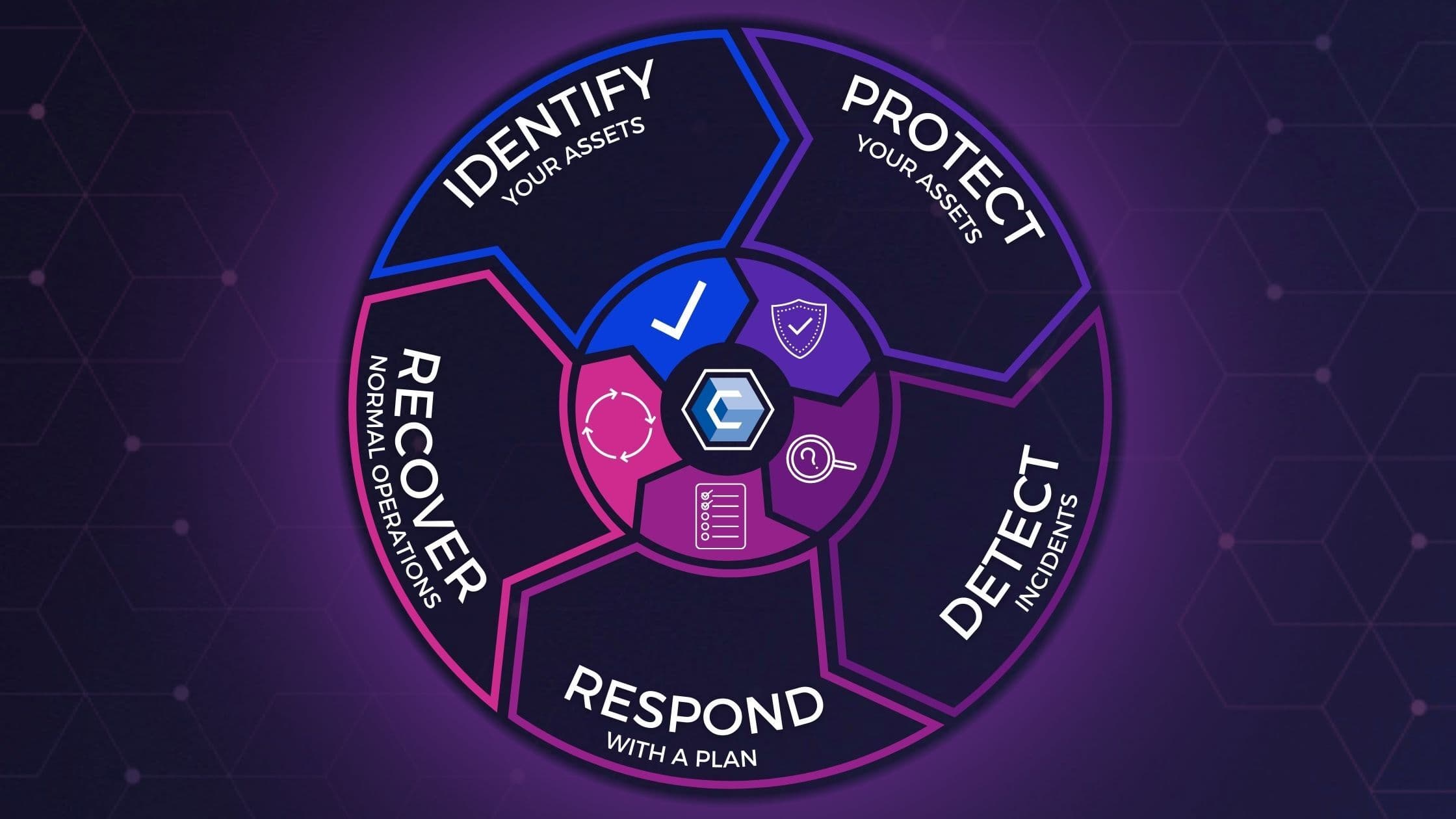
Reviewing The 5 Stages Of The Cybersecurity Lifecycle EXAMPLES

Cyber Security In Software Development 12 Outsourcing Tips

Security 101 Protecting Against The Most Common Cyber Attacks

Cybersecurity Tips For Small Businesses

Cyber Security Saiba O Que Faz Um Profissional De Ciberseguran a