Network Security Attacks In Computer Networks
It’s easy to feel scattered when you’re juggling multiple tasks and goals. Using a chart can bring a sense of structure and make your daily or weekly routine more manageable, helping you focus on what matters most.
Stay Organized with Network Security Attacks In Computer Networks
A Free Chart Template is a useful tool for planning your schedule, tracking progress, or setting reminders. You can print it out and hang it somewhere visible, keeping you motivated and on top of your commitments every day.

Network Security Attacks In Computer Networks
These templates come in a variety of designs, from colorful and playful to sleek and minimalist. No matter your personal style, you’ll find a template that matches your vibe and helps you stay productive and organized.
Grab your Free Chart Template today and start creating a more streamlined, more balanced routine. A little bit of structure can make a huge difference in helping you achieve your goals with less stress.

Types Of Cyber Security Attacks Types Of Cyber Security What Is Cyber
Mar 28 2023 nbsp 0183 32 What is a computer network A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other A network Jul 10, 2025 · Discover what is a network is, its types, topologies, and real-world computer network examples. Learn how networks power business communication and cybersecurity.
Hacking Attacks
Network Security Attacks In Computer NetworksOct 5, 2020 · What is a network? In information technology, a network is defined as the connection of at least two computer systems, either by a cable or a wireless connection. The … A computer network is a collection of communicating computers and other devices such as printers and smart phones Today almost all computers are connected to a computer network
Gallery for Network Security Attacks In Computer Networks

The Network

Cyber Attack Cheat Sheet Infographic

Dos Attack

Network Attacks And Cyber Security Threats

Security Zines Network Attacks Vrogue co

Cyber Network Attack
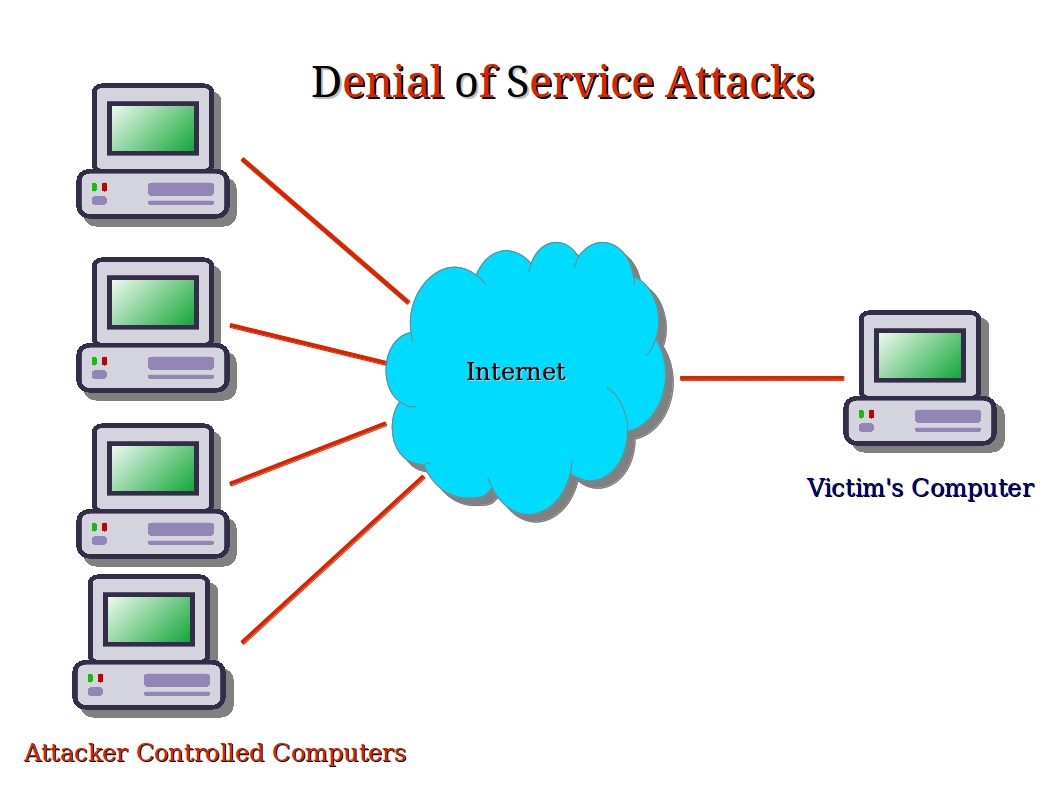
Denial Of Service On Rsyslog Checkpoint Sourceslasopa
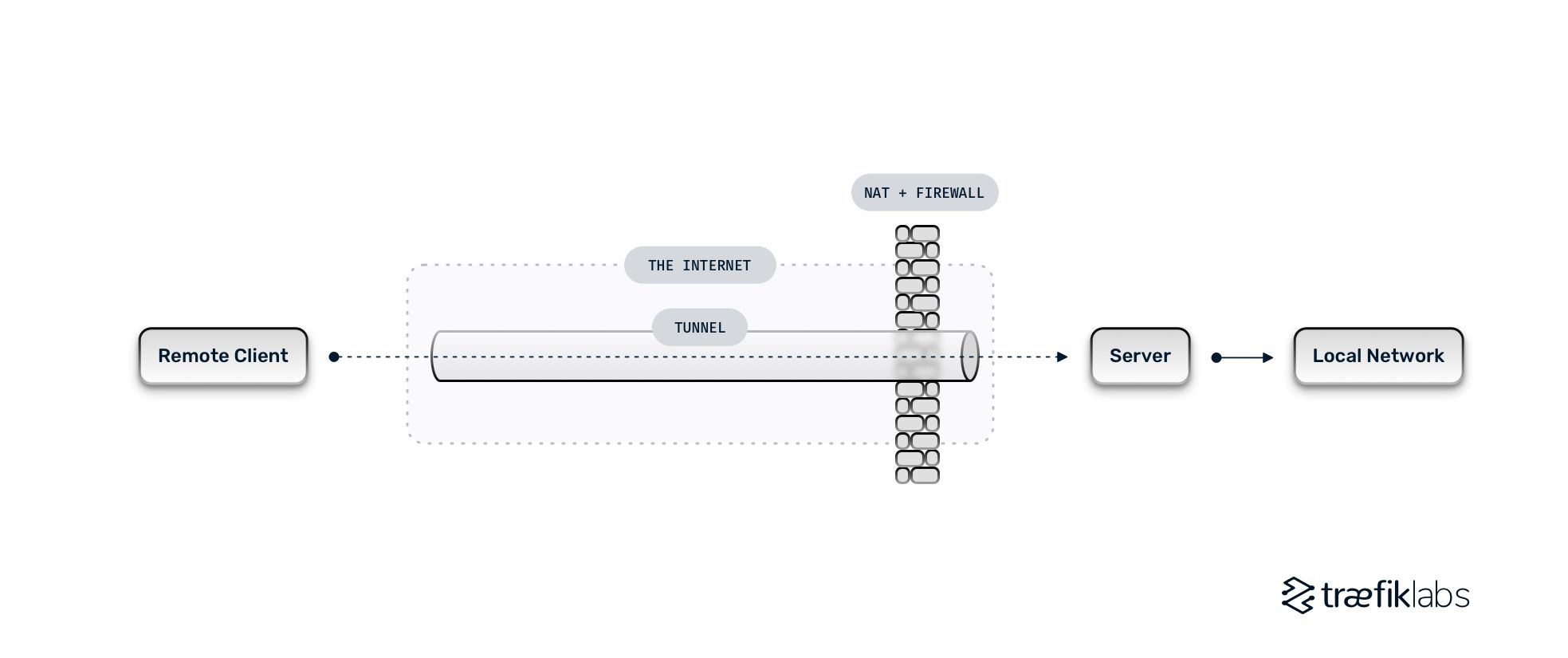
What Is Network Tunneling How Is It Used Traefik Labs
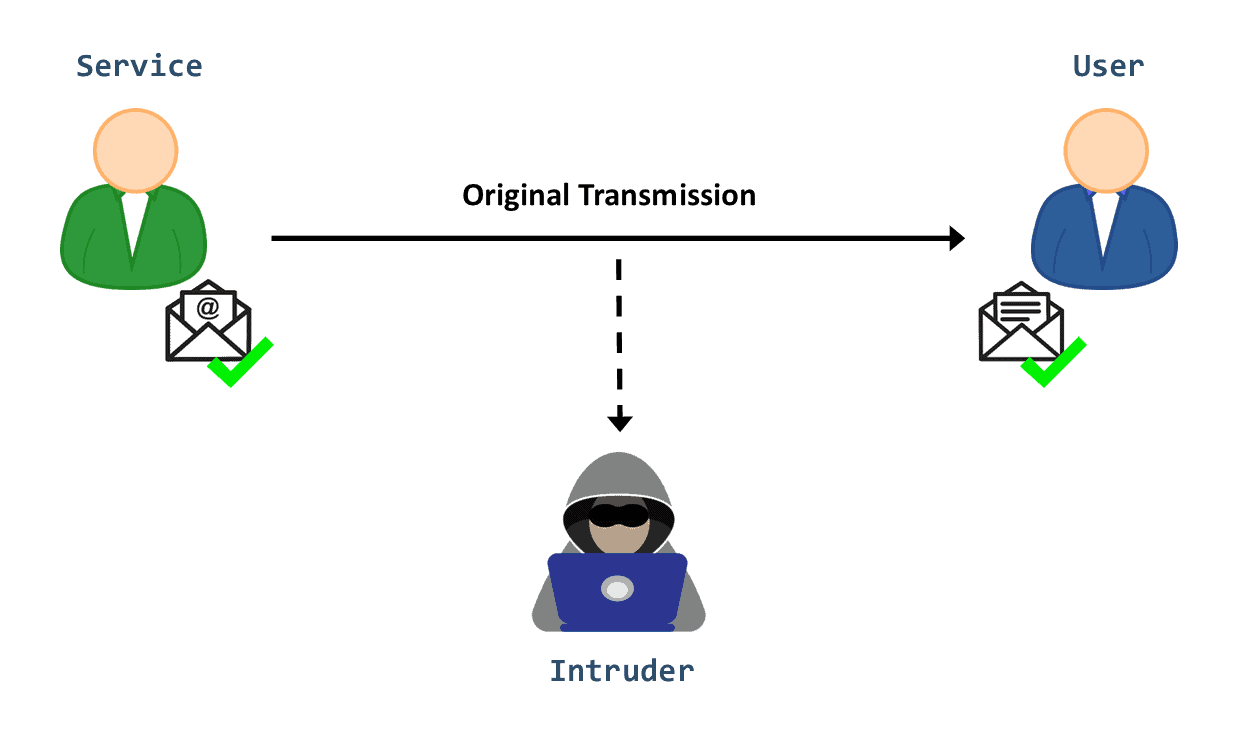
Security Interruption Vs Interception Vs Modification Vs
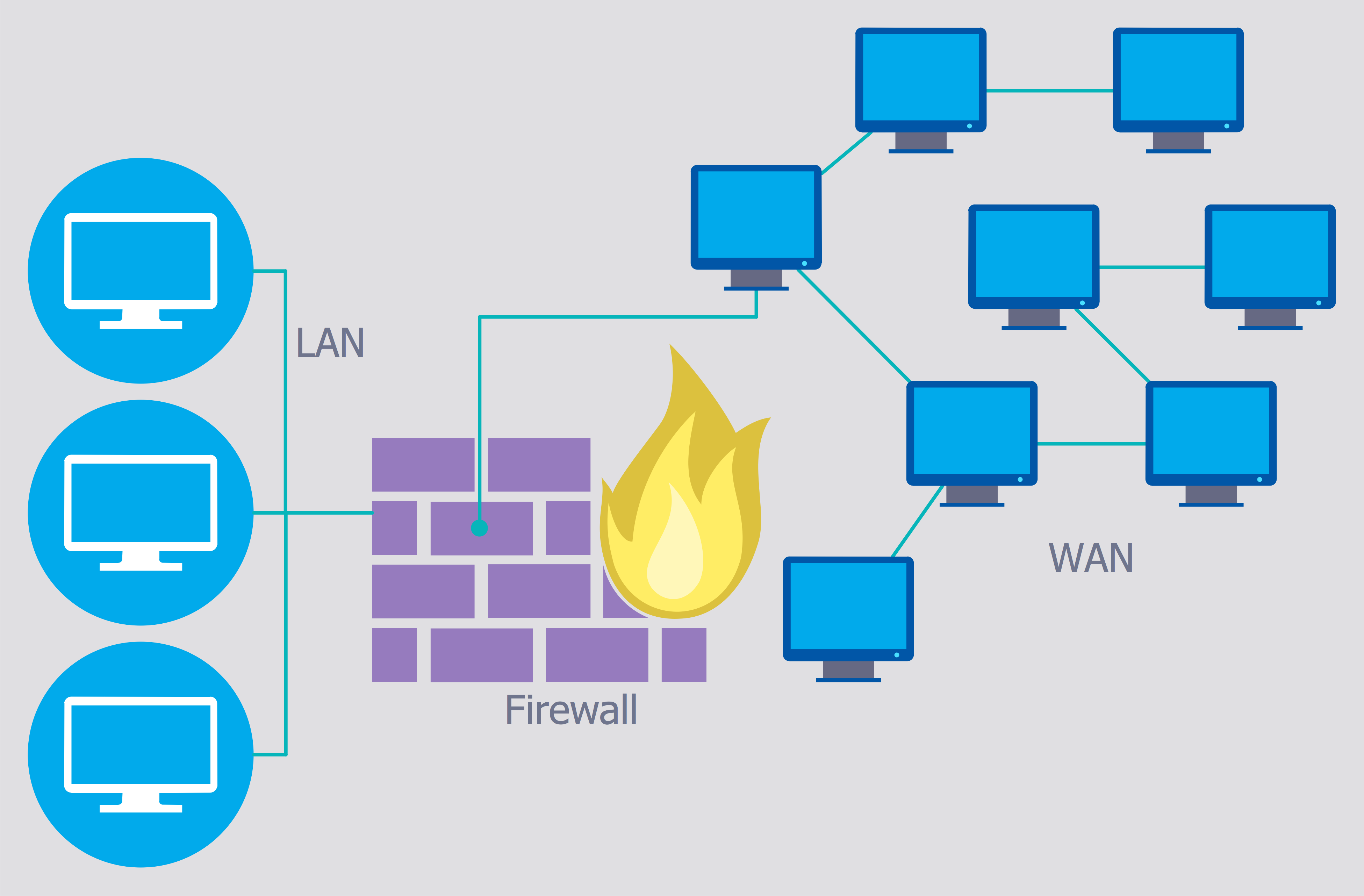
Diagram Of Network Security
