Differentiate Between Cybercrime And Cyber Attacks
It’s easy to feel scattered when you’re juggling multiple tasks and goals. Using a chart can bring a sense of structure and make your daily or weekly routine more manageable, helping you focus on what matters most.
Stay Organized with Differentiate Between Cybercrime And Cyber Attacks
A Free Chart Template is a useful tool for planning your schedule, tracking progress, or setting reminders. You can print it out and hang it somewhere visible, keeping you motivated and on top of your commitments every day.

Differentiate Between Cybercrime And Cyber Attacks
These templates come in a variety of designs, from colorful and playful to sleek and minimalist. No matter your personal style, you’ll find a template that matches your vibe and helps you stay productive and organized.
Grab your Free Chart Template today and start creating a more streamlined, more balanced routine. A little bit of structure can make a huge difference in helping you achieve your goals with less stress.

6 Common Types Of Cyber Attacks
Differ quot quot Differentiate quot 【ネイティブ回答】「disting...」と「differe...」はどう違うの?質問に7件の回答が集まっています!Hinativeでは"英語(アメリカ)"や外国語の勉強で気になったことを、ネイティブスピー …

Dos Attack
Differentiate Between Cybercrime And Cyber AttacksĐồng nghĩa với distinguish 1) Differentiate - to describe the differences between two objects. - when this word is used, what is important are the differences between the objects. Example 1: … Differentiate to recognize or express the difference between things or people For example quot It s sometimes hard to differentiate one sample from another quot Distinguish to recognize or
Gallery for Differentiate Between Cybercrime And Cyber Attacks
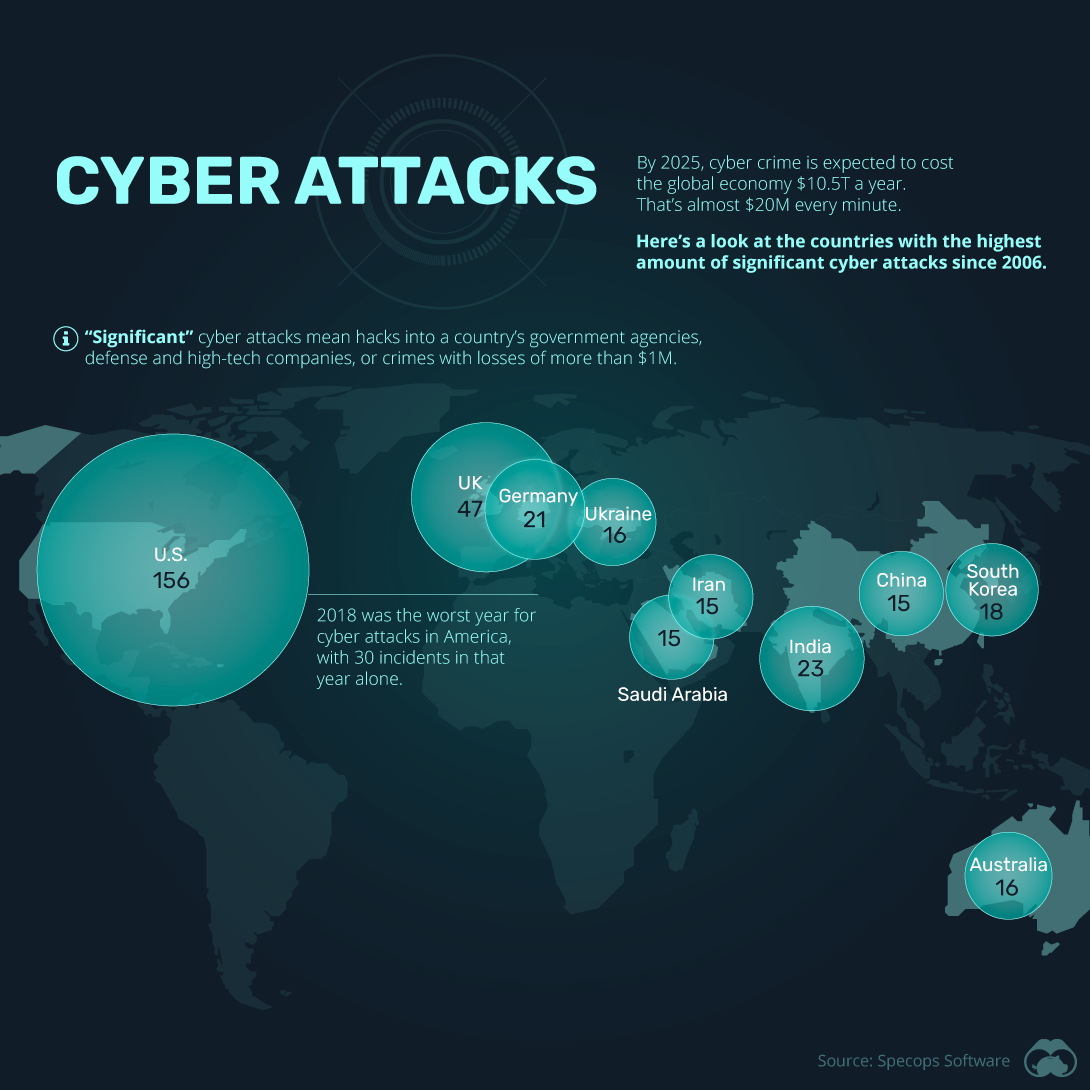
Cyber Breach 2024 Alexi Austina

Statista 2022

Cyber Attack Statistics

Cyber Attack Statistics

Cyber Security Background
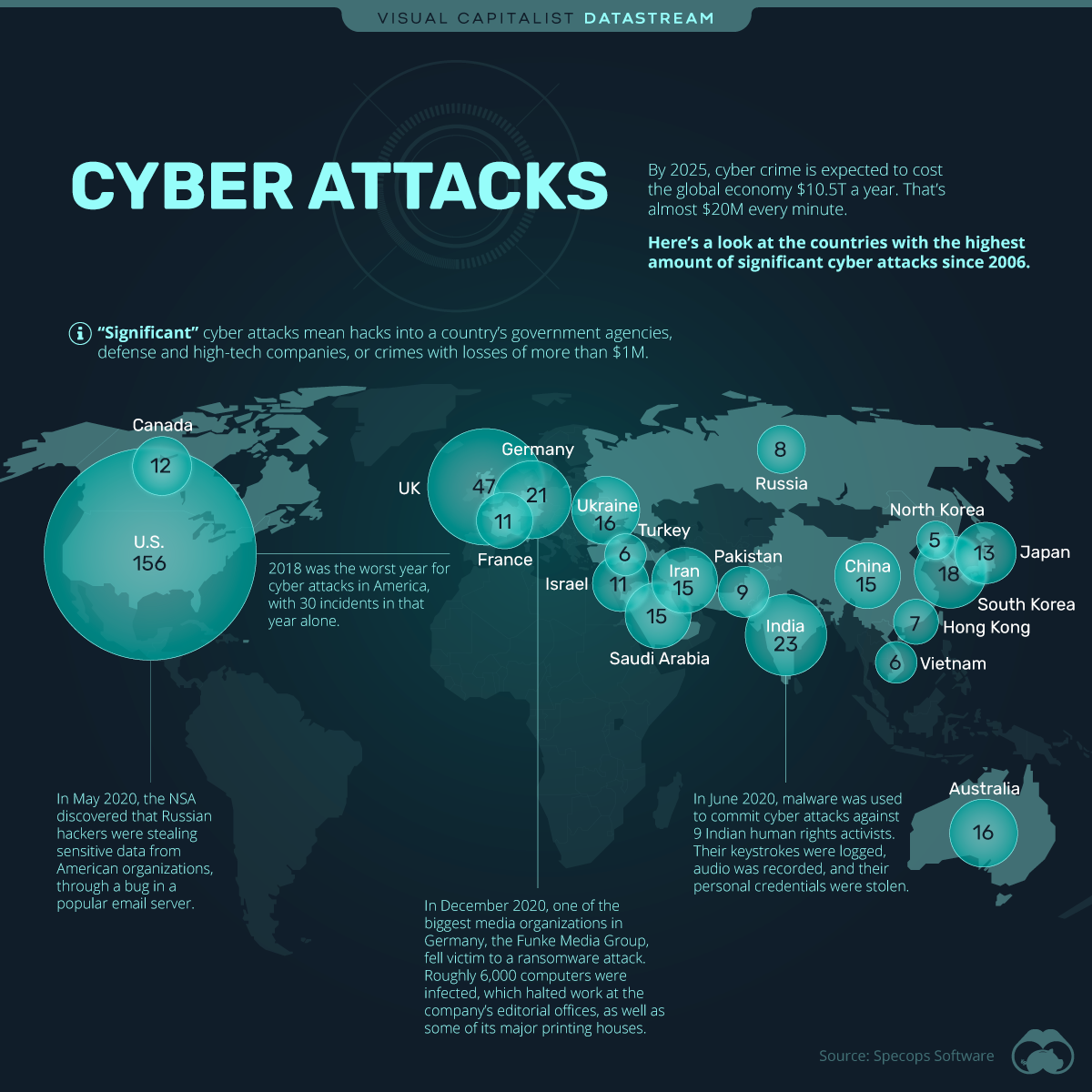
Ranked The Most Significant Cyber Attacks From 2006 2020 By Country
Cyber Crime Banner Royalty Free Vector Image VectorStock

Alarming Rise In Cyberattacks Plagues Healthcare Industry KnowBe4

Understanding A Phishing Attack

Active And Passive Attacks In Cyber Security