Attack Computer Network Security
It’s easy to feel scattered when you’re juggling multiple tasks and goals. Using a chart can bring a sense of structure and make your daily or weekly routine more manageable, helping you focus on what matters most.
Stay Organized with Attack Computer Network Security
A Free Chart Template is a great tool for planning your schedule, tracking progress, or setting reminders. You can print it out and hang it somewhere visible, keeping you motivated and on top of your commitments every day.

Attack Computer Network Security
These templates come in a variety of designs, from colorful and playful to sleek and minimalist. No matter your personal style, you’ll find a template that matches your vibe and helps you stay productive and organized.
Grab your Free Chart Template today and start creating a smoother, more balanced routine. A little bit of structure can make a big difference in helping you achieve your goals with less stress.

LockBit leaked DC City Agency Data From Third Party SC Media
0x01 Hash Flooding Attack Denial of Service 早在题主提问的2013年,估计谁都猜不到「進撃の巨人」这个标题到底指的是什么,根据开篇部分的情节,西方人理解成attack on titan也貌似合理。

120 Ddo Stock Photos Pictures Royalty Free Images IStock
Attack Computer Network SecurityFeb 28, 2023 · What did he suffer? A heart attack. In the OP's sentence, the verb is intransitive, and therefore needs a preposition. Why the difference? We use "to suffer from X" to convey the … Jun 28 2014 nbsp 0183 32 I d say quot attack on quot is used when the target is something concrete attack on the World Trade Center buildings and quot attack against quot when the target is something more abstract
Gallery for Attack Computer Network Security
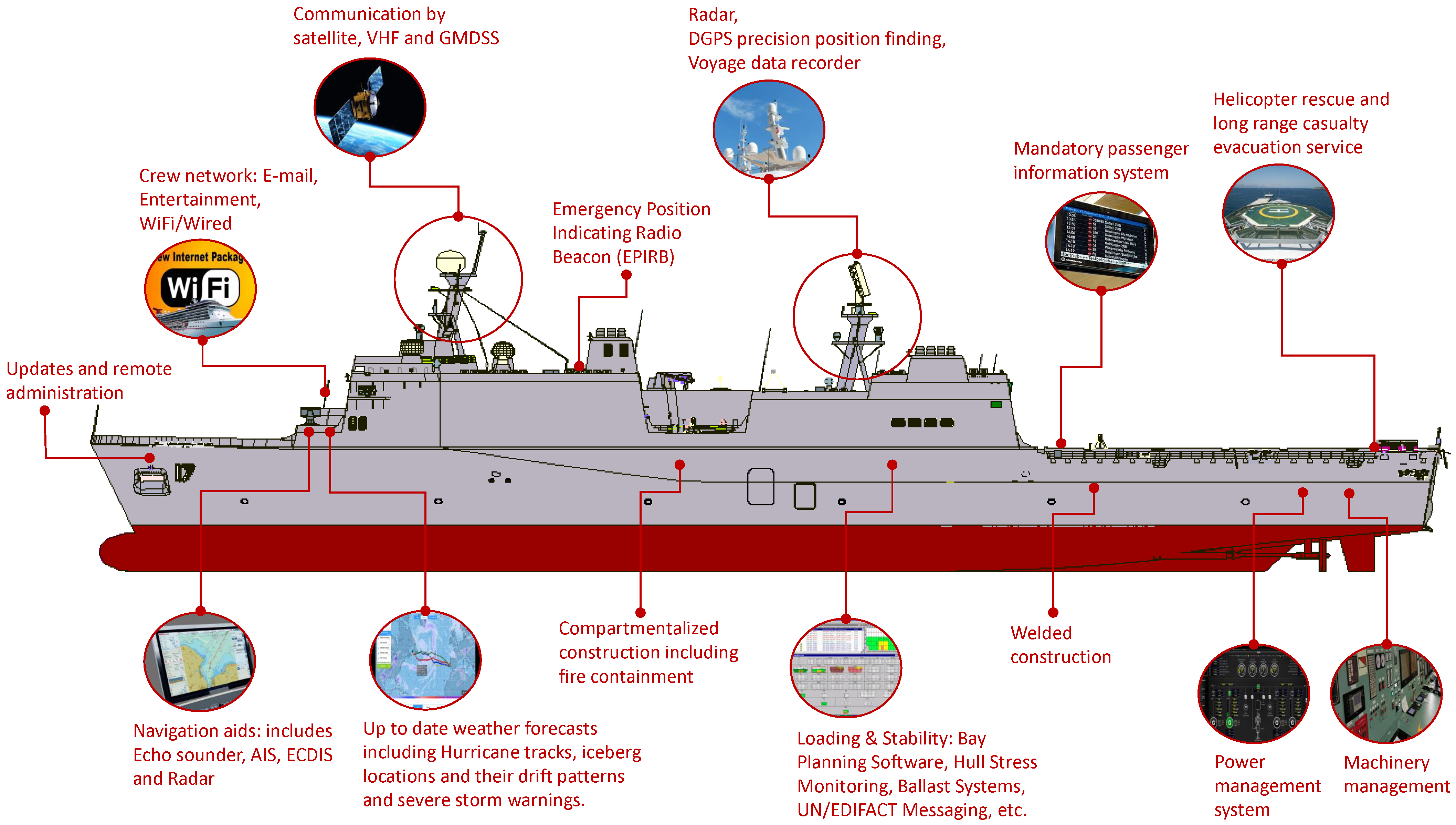
Network Free Full Text Cybersecurity Challenges In The Maritime Sector

What Is A Cyber Attack Definition Types Prevention Forbes Advisor
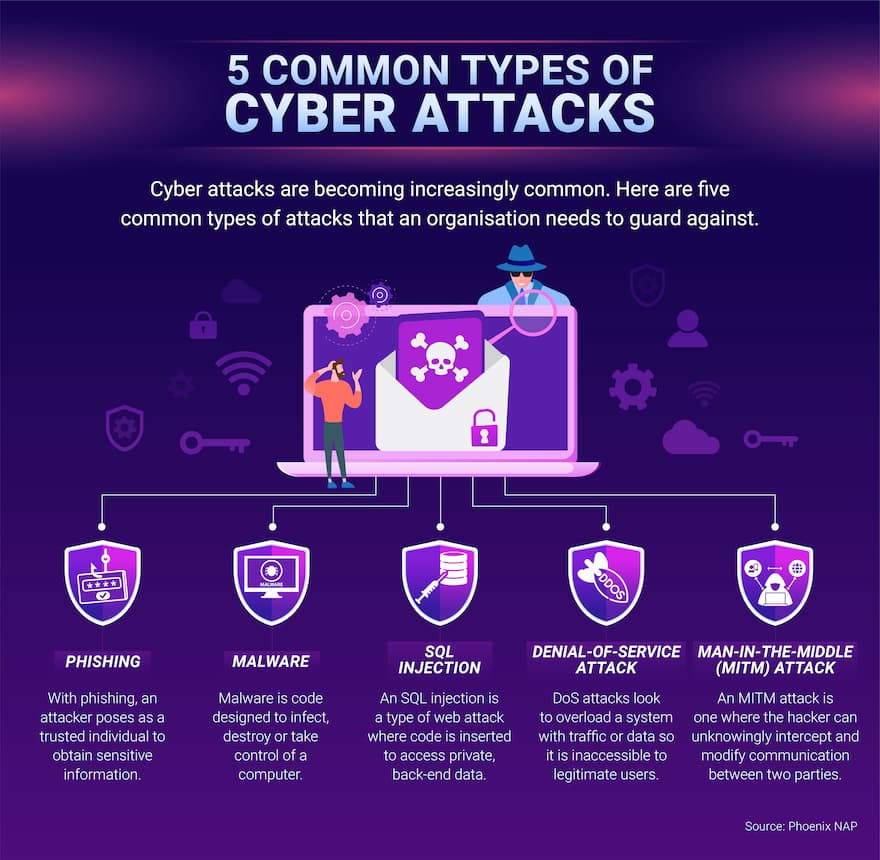
Cyber Attacks Tips For Protecting Your Organisation ECU Online

What Is A Cyber Attack Recent Examples Show Disturbing Trends CSO Online
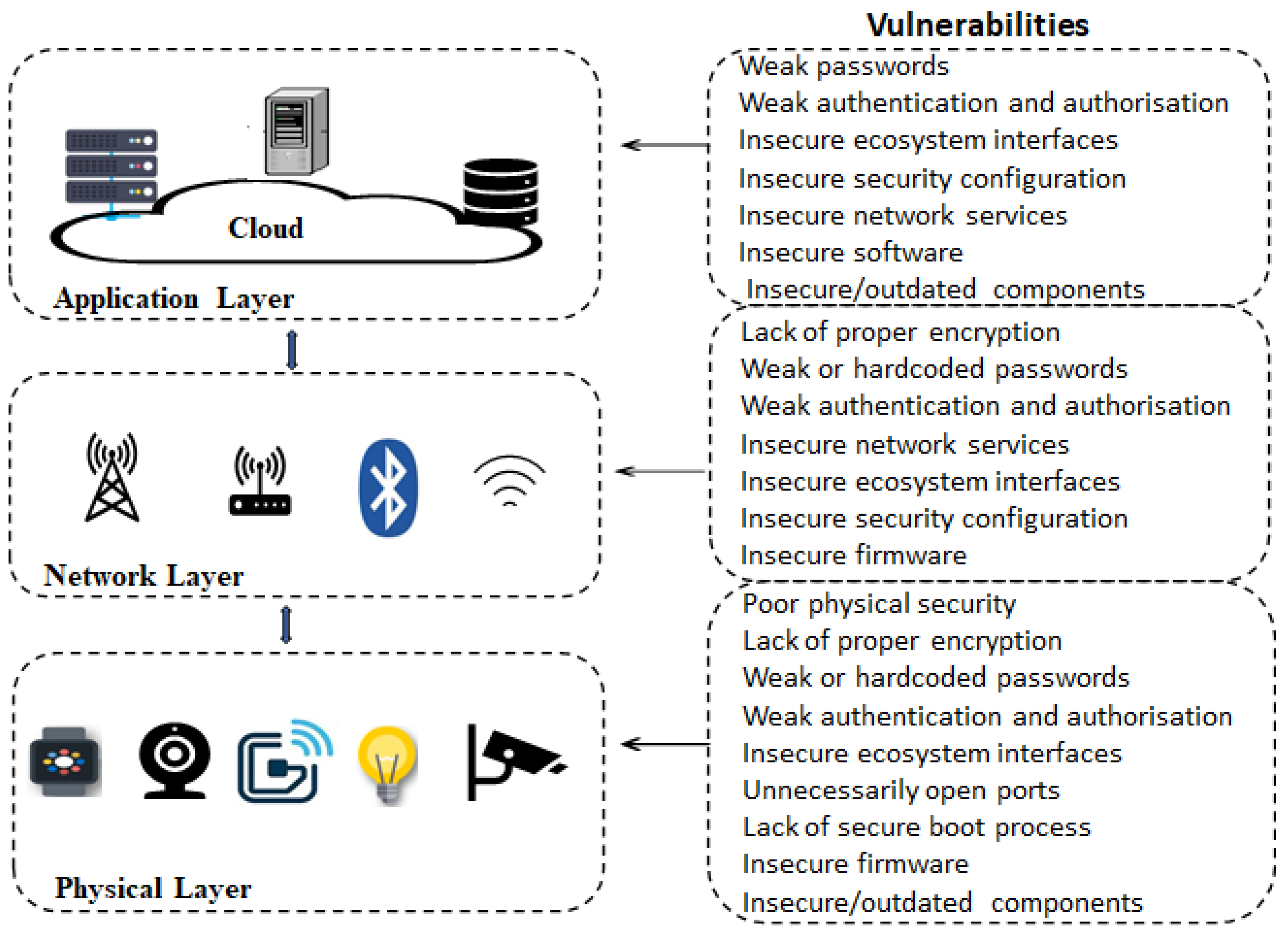
Electronics Free Full Text Analysis Of Consumer IoT Device
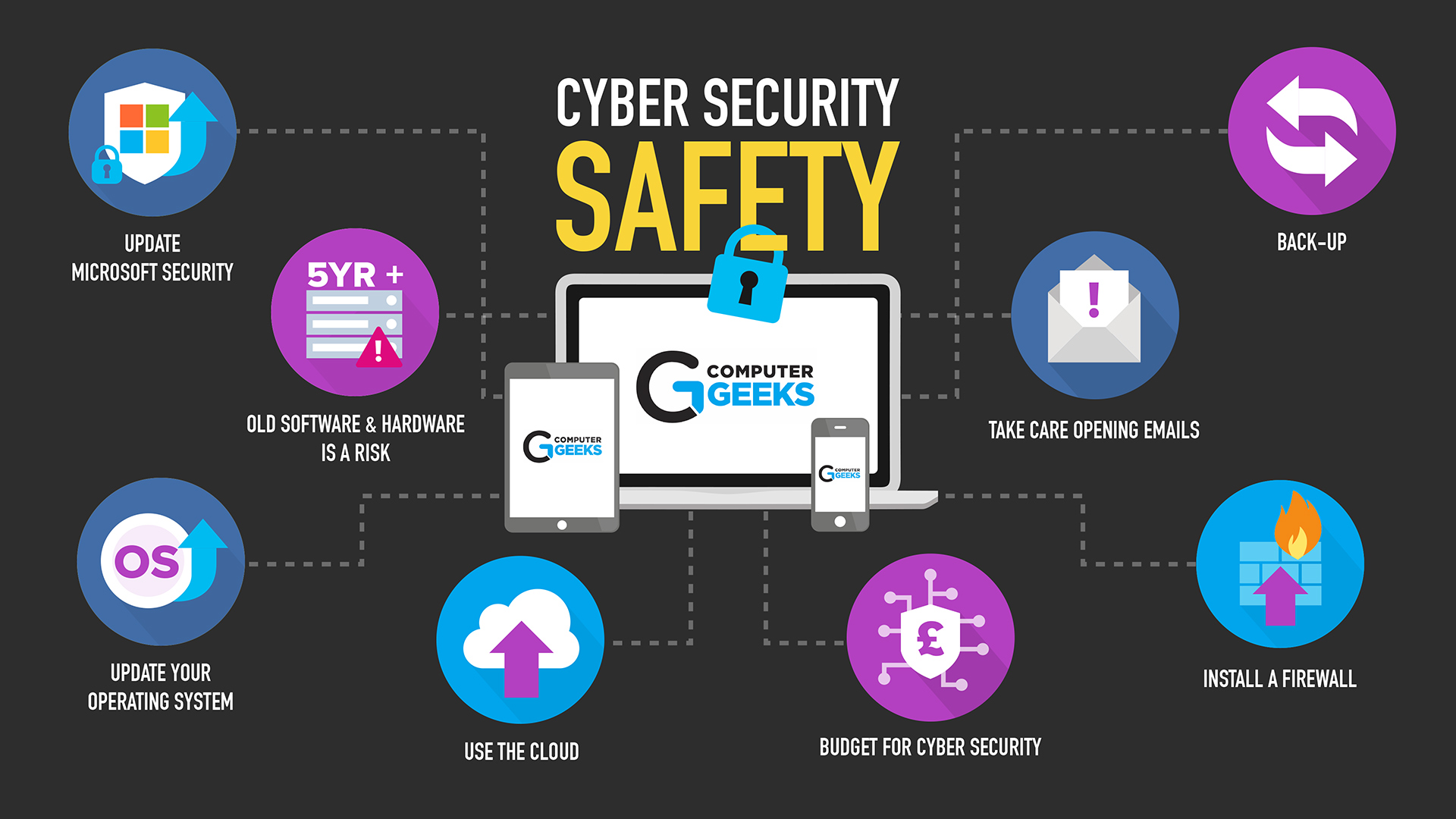
How To Defend Your Business Against Cyber Attacks Computer Geeks

Wireless Sensor Network Security A Recent Review Based On State of the
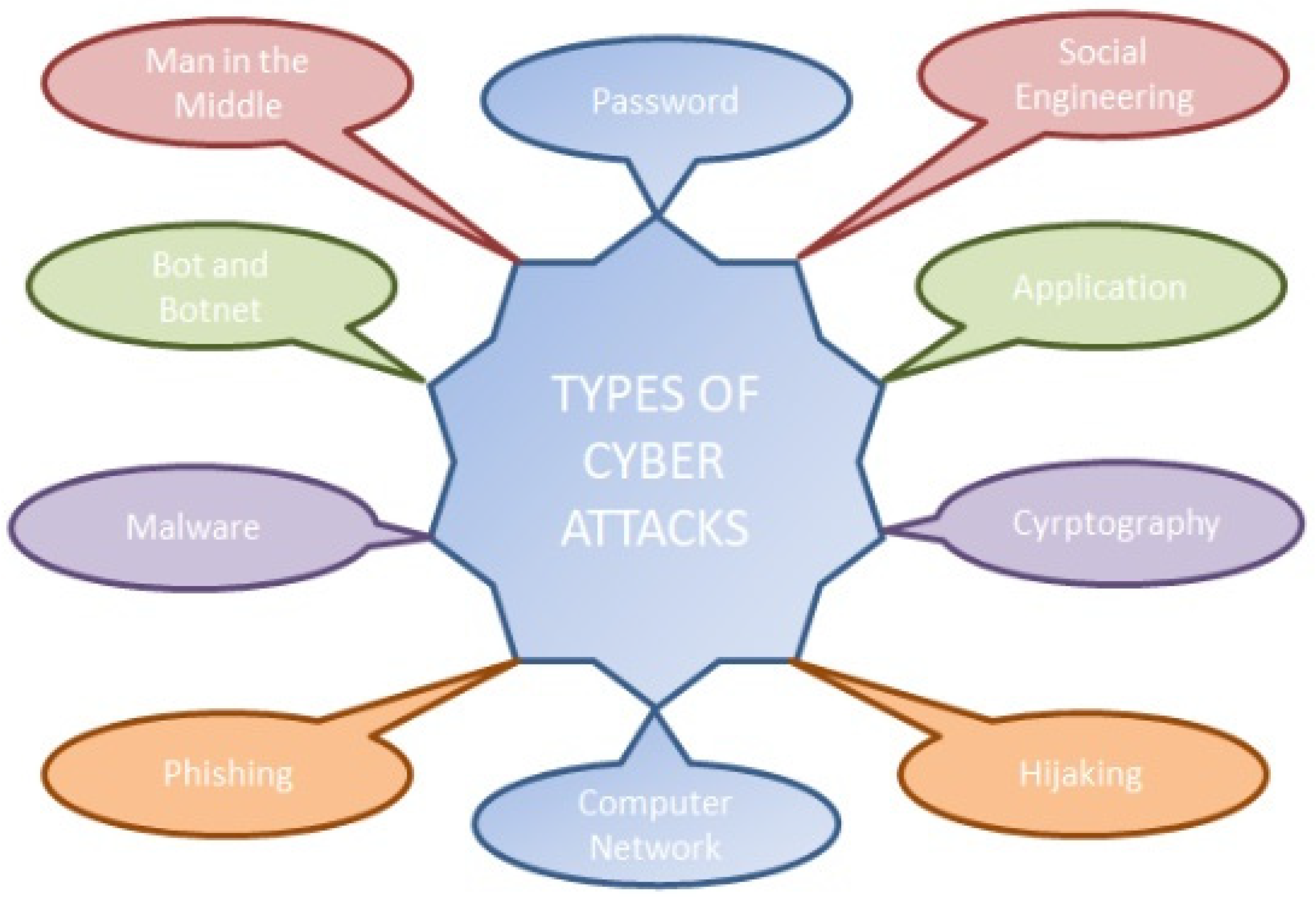
Electronics Free Full Text A Comprehensive Review Of Cyber Security
Analysisof Pingof Death Do Sand DDo SAttacks PDF Denial Of Service

Chapter 21 Security Beyond Computer Networks Information Assurance
